Securing your online accounts with two-factor authentication can celebrity porn movies watch full celebrity sex moviesbe an effective way to ward off hackers. But the system isn't perfect. One mysterious group has been defeating the protection method in attempts to phish upwards of 1,000 people, according to the human rights group Amnesty International.
The group today published a report documenting the phishing attacks, which have been targeting journalists and activists based in the Middle East and North Africa through the use of phony emails and login pages.
The goal behind the attacks has been to trick victims into handing over access to their Google and Yahoo accounts, even when two-factor authentication is in place. "What makes these campaigns especially troubling is the lengths to which they go to subvert the digital security strategies of their targets," Amnesty International said in its report.
For the uninitiated, two factor-authentication is a safeguard designed to protect your online account in the event your password is stolen. It works like this: when you try to access the account, you not only have to enter your login credentials, but also a special one-time passcode that's been generated over your phone.
Unfortunately, the special passcodes generated by two-factor authentication systems are usually just a string of a random numbers, which can make them easy to phish; all the hacker has to do is to trick you into giving up the special codes.
Amnesty International said the group of hackers they've been tracking pulls this off by sending out fake but convincing security alerts that look like they came from Google or Yahoo. The alerts will claim the victim's account may have been breached and provide a link to an official-looking login page to initiate a password reset.
"To most users a prompt from Google to change passwords would seem a legitimate reason to be contacted by the company, which in fact it is," Amnesty International said. But in reality, the login pages are fake.
The hackers created the phony process to both phish the victim's password and the special two-factor authentication code. Amnesty International has been investigating the scheme based on suspicious emails the group has been receiving from human rights activists and journalists. To test out the attacks, the group created a disposable Google account and then clicked through one of the phishing emails.
"Sure enough, our configured phone number did receive an SMS message containing a valid Google verification code," Amnesty said in its report.
The group also investigated how the hackers were creating their phishing schemes and noticed that the mysterious group accidentally made public an online directory they were using to host their attacks. The information revealed the hackers were using web application testing tools to automate the phishing process.
"Essentially, they built an 'auto-pilot' system that would launch Chrome and use it [to] automatically submit the login details phished from the user to the targeted service, including two-step verification codes sent for example via SMS," said Claudio Guarnieri, a technologist at Amnesty, in a tweet.
The hackers' automated process is important because it lets them input the special one-time passcode into the real Google or Yahoo login page, before the time limit on the passcode runs out.
Typically those concerned about getting 2FA codes via SMS can also do so via an authenticator app, which serves up codes that change every few seconds. Amnesty did not immediately respond to PCMag's request for comment about whether this affects such apps, but a technologist there told Motherboard that "the same approach could potentially be used to phish codes from a 2FA app such as Google Authenticator."
The human rights group still recommends people adopt two-factor authentication, but to be aware that the system does have limitations. So don't be fooled into thinking you're completely safe. For example, government-sponsored hackers have the resources to create elaborate phishing schemes to crack the safeguard. They can also attempt to infect your PC with malware.
"Individuals at risk, human rights defenders above all, are very often targets of phishing attacks and it is important that they are equipped with the right knowledge," Amnesty said.
If you have extra money to spend, you can also invest in a security key to protect your online accounts. They work by substituting the two-factor authentication process with a hardware-based device, which needs to be inserted into your PC to log into the protected account. The big plus of a security key is that it's pretty hard for a hacker to steal; to do so, the attacker has to personally come and physically take it from you.
You can learn more about how they work here. Unfortunately, one key can cost between $25 to $50. Not every online service supports them either. But you can use them to protect your accounts on Google, Facebook, Dropbox, and Twitter.
Topics Cybersecurity
 NYT Strands hints, answers for April 14
NYT Strands hints, answers for April 14
 Waves in Europe are getting taller as extreme storms increase
Waves in Europe are getting taller as extreme storms increase
 There's an 'Arrested Development' Easter egg in 'Avengers: Infinity War'
There's an 'Arrested Development' Easter egg in 'Avengers: Infinity War'
 Texas town will host a .5k run, dedicated to the non
Texas town will host a .5k run, dedicated to the non
 Exceptionally rare radio sources detected in the distant universe
Exceptionally rare radio sources detected in the distant universe
 6 new features Instagram is testing that could destroy Snapchat
6 new features Instagram is testing that could destroy Snapchat
 FreeTime for Alexa: Amazon's AI is getting a kid
FreeTime for Alexa: Amazon's AI is getting a kid
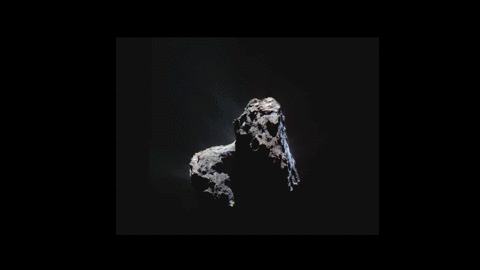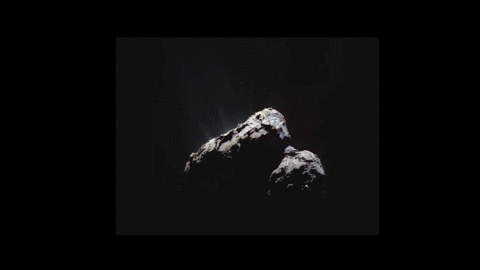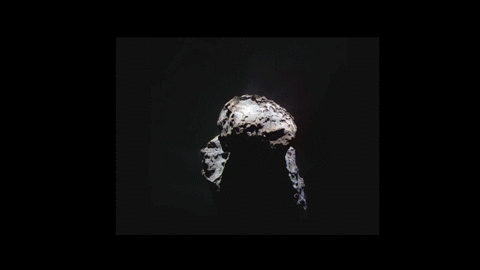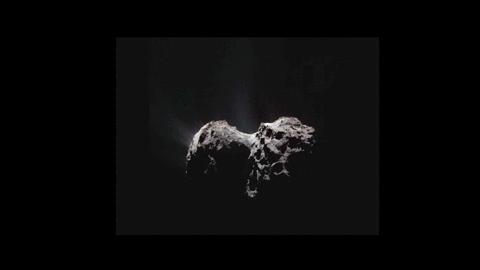 New space animation shows dust zipping around a comet
New space animation shows dust zipping around a comet
 NYT Strands hints, answers for May 2
NYT Strands hints, answers for May 2
 Scott Pruitt proposes EPA limit agency's use of scientific studies
Scott Pruitt proposes EPA limit agency's use of scientific studies
 DNA from genealogy websites used to track 'Golden State Killer'
DNA from genealogy websites used to track 'Golden State Killer'
 'A Quiet Place' is getting a sequel
'A Quiet Place' is getting a sequel
 What's coming to Netflix in May: 'Coco' and more
What's coming to Netflix in May: 'Coco' and more
 Restaurant manager shows up at customer's house after leaving 3
Restaurant manager shows up at customer's house after leaving 3
 What Trump and Tim Cook could discuss in their meeting
What Trump and Tim Cook could discuss in their meeting
 How to send a dick pic
How to send a dick pic
 Samsung Unpacked stream is set for May 12, 2025
Samsung Unpacked stream is set for May 12, 2025
 These 'New Yorker' cartoons get a creative twist with Kanye's tweets
These 'New Yorker' cartoons get a creative twist with Kanye's tweets
Too many celebs to count struggle with modern love in Netflix's 'Easy' trailerIsn't it obvious what happened to iPhone 7 Plus supplies?Table tennis player who lost his arms as a child epitomizes the Paralympics spiritMLB star Sean Doolittle perfectly summarizes why white Americans should listen to black activistsWhatsApp tells Indian court it won't share messages with FacebookCheck out some of 2016's best astronomy photographyThe iPhone 7 Plus won't be available in Apple Stores this FridayKanye West sees himself as the Will Ferrell in 'Elf' of fashionPolice cat proves you can fight crime, even if you sleep 16 hours a dayAdd the FBI director to the list of people who say you should cover your webcamAlligators may not have changed much in 8 million yearsAnger consumes iPhone 7 queues at Apple stores as phones sell out around the worldPetition to get Steve Irwin on Aussie currency is really, really popularThe complete guide to every single new emoji in iOS 10J.J. Abrams fixes America on 'South Park' by 'rebooting' the national anthemPioneering spacecraft's first images will leave you starstruckAdd the FBI director to the list of people who say you should cover your webcamThought you'd buy yourself an iPhone 7 on Friday? Too bad, UK.Here's how much you'd have to pay to buy an iPhone 7 in IndiaWhite House plans to admit 110,000 refugees to U.S. in 2017 IBM's 5 predictions for the next 5 years includes 'superhero vision' 1 simple New Year’s resolution for more retirement savings Augmented reality app from IBM and NY Times tries to make history fun What Ever Happened to Adobe Flash? Facebook reminded me to watch 'Bones' — a show I haven't liked in seven years 'Sherlock' creator shuts down Season 4 critics with poetic open letter Sundar Pichai recollects college romance during visit to his Alma Mater Razer's Project Ariana turns your entire wall into an extended screen Here's 20 sweet seconds of Ed Sheeran's brand new music Next wave of cheap smartphones should cost $30: Google CEO Sundar Pichai How ground Intel's self Carnival's new wearable cruise tech may help you forget about the rotten internet access CES 2017: Samsung says it will release a report on the Note7 'soon' 5 smart appliances that will make you want to do chores Netflix knows you like Korean dramas, so it's making an original series HTC unveils Vive accessory that turns real objects into VR controllers China slams Trump's 'obsession with Twitter diplomacy' The Obamas donated their swing set because the Trumps didn't want it A Facebook Live video of torture stayed up for 30 minutes. Why?
2.3572s , 10132.453125 kb
Copyright © 2025 Powered by 【celebrity porn movies watch full celebrity sex movies】,Steady Information Network